The Role of Mathematics in Cryptography
In today’s digital world, cryptography is essential for securing sensitive information, from online banking transactions to private messages. But have you ever wondered how it works? At its core, mathematics in cryptography plays a crucial role in protecting data through encryption, decryption, and secure key management.
This guide explores the mathematical foundations of cryptography, including prime numbers, modular arithmetic, hash functions, and elliptic curves, and how they keep your data safe.
What is cryptography?
Cryptography is the science of encoding and decoding information to ensure:
✔ Confidentiality – Data remains private and unreadable to unauthorized users.
✔ Integrity – Information remains unchanged during transmission.
✔ Authentication – Verifies the sender’s identity to prevent fraud.
How Mathematics Powers Cryptography
At its core, mathematics in cryptography enables secure communication by using:
🔹 Encryption – Converting readable data (plaintext) into unreadable data (ciphertext).
🔹 Decryption – Reversing ciphertext back into plaintext using a key.
🔹 Keys – Complex mathematical values used to encrypt and decrypt messages securely.
🔗 Related Resource: Understanding Encryption and Decryption
Key Mathematical Concepts in Cryptography
Mathematics is the backbone of cryptography. Here are the essential concepts:
1. Prime Numbers: The Foundation of Secure Keys
Prime numbers are used in cryptographic algorithms like RSA encryption. Their unique properties make them ideal for secure key generation.
Example:
- Take two prime numbers:
5 and 7
- Multiply them:
5 × 7 = 35
- Factoring 35 back into its original primes is easy, but with very large prime numbers, it becomes computationally difficult—making cryptographic keys secure.
🔗 Related Resource: Why Prime Numbers Matter in Cryptography?
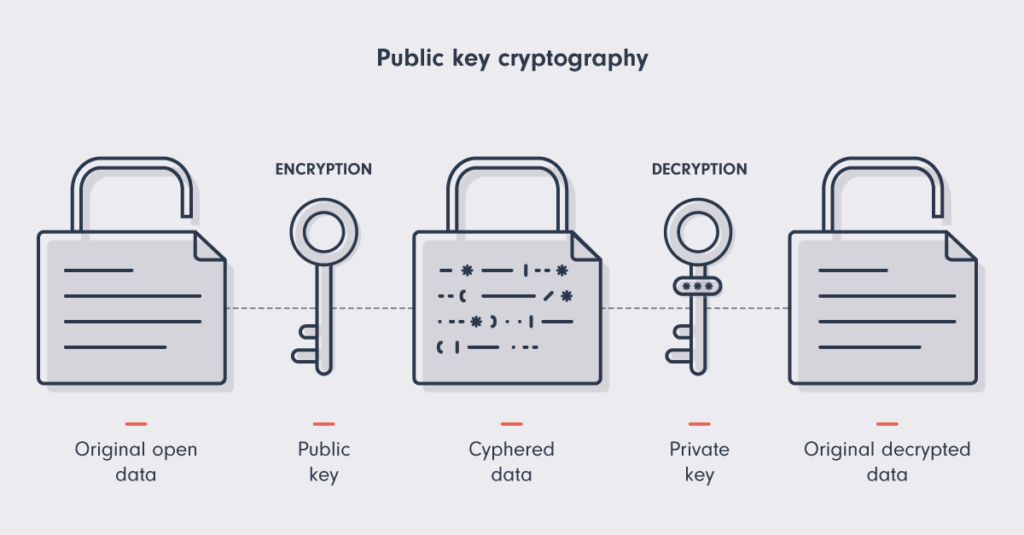
2. Public & Private Key Cryptography
Cryptographic systems use asymmetric encryption, meaning two keys are involved:
✔ Public Key: Used for encryption (shared openly).
✔ Private Key: Used for decryption (kept secret).
Example:
In RSA encryption, the public key is a product of two large prime numbers, while the private key is derived from those primes.
🔗 Related Resource: Understanding Public & Private Key Cryptography
3. Modular Arithmetic: The Core of Encryption
Modular arithmetic works with remainders and is used in Diffie-Hellman key exchange and RSA encryption.
Example:
17 mod 5 = 2
(17 divided by 5 leaves a remainder of 2)
This property helps create one-way functions that are easy to compute but difficult to reverse—a crucial feature of cryptographic security.
🔗 Related Resource: How Modular Arithmetic Works?
4. Elliptic Curve Cryptography (ECC): Faster & More Secure
Elliptic Curve Cryptography (ECC) is an advanced encryption method that uses algebraic structures. It creates smaller, more efficient keys compared to traditional RSA encryption.
Example:
An elliptic curve equation:
y2 = x3 + ax + b
Points on the curve are used to generate cryptographic keys.
🔗 Related Resource: Introduction to Elliptic Curve Cryptography
5. Hash Functions: Ensuring Data Integrity
A hash function converts data into a fixed-length string of characters. Even a small change in input produces a completely different hash—making it impossible to reverse.
Example:
The SHA-256 hash of “hello”:
2cf24dba5fb0a30e26e83b2ac5b9e29e1b161e5c1fa7425e73043362938b9824Hash functions are widely used for password protection, blockchain security, and digital signatures.
🔗 Related Resource: How Hash Functions Work
How Mathematics in Cryptography Protects Your Data
To see how encryption works, let’s look at a simple cryptographic technique:
The Caesar Cipher (Basic Encryption Example)
Encryption:
- Shift each letter forward by a fixed number.
- With a shift of 3:
- A → D, B → E, C → F
- “HELLO” becomes “KHOOR”.
Decryption:
- Shift letters back by the same number.
- “KHOOR” → “HELLO”.
🔗 Related Resource: Understanding the Caesar Cipher
Real-World Applications of Cryptography
Mathematics in cryptography secures various fields, including:
✔ Banking Transactions: Encrypts sensitive data in online banking.
✔ Messaging Apps: WhatsApp & Signal use end-to-end encryption.
✔ Blockchain Technology: Secures Bitcoin and other cryptocurrencies.
✔ Military & Government: Protects classified information.
🔗 Related Resource: Real-World Uses of Cryptography
Challenges & Future of Mathematics in Cryptography
Challenges in Cryptography
- Quantum Computing: Could break current encryption methods.
- Key Management: Storing and sharing cryptographic keys securely.
- Human Error: Weak passwords or improper encryption implementation.
The Future of Cryptography
- Post-Quantum Cryptography – Developing encryption that withstands quantum attacks.
- Zero-Knowledge Proofs – Allows secure authentication without revealing any information.
🔗 Related Resource: How Quantum Computing Affects Cryptography
FAQs About Mathematics in Cryptography
What’s the difference between encryption and hashing?
- Encryption is reversible (you can decrypt it), while hashing is one-way (you can’t reverse it).
Can cryptography be broken?
- Some encryption methods can be cracked with enough computing power, but modern cryptography is highly secure.
Why are prime numbers used in cryptography?
- Their uniqueness and difficulty to factor make them ideal for secure key generation.
What role does math play in blockchain?
- Mathematics ensures secure transactions and data integrity in blockchain networks.
🔗 Related Resource: Cryptography in Blockchain
📢 Final Thoughts
Cryptography is a perfect blend of mathematics and technology that protects our digital world. By understanding mathematics in cryptography, you can appreciate the complexity and security behind encryption methods.
Whether you’re a student, tech enthusiast, or cybersecurity professional, learning how math secures data is essential in today’s world.
Ready to Explore More?
🔗 Learn More About Cryptography & Math
🔗 Try Our Interactive Cryptography Challenges
Let’s unlock the secrets of mathematics in cryptography together!






